Artificial Intelligence
The group is interested in the study of novel methods in AI and their security issues. The key researches are two-folded: 1) AI security, including adversarial examples, neural network backdoors, neural network model watermarking, etc. 2) chatbot in social media based on AI technology.
learning resource
Neural Network Watermarkingpublication
- Forward Creation, Reverse Selection: Achieving Highly Pertinent Multimodal Responses in Dialogue ContextProceedings of the 32st ACM International Conference on Information & Knowledge Management, 2023.
- Physical Invisible Backdoor Based on Camera ImagingMM '23: Proceedings of the 30th ACM International Conference on Multimedia, 2023.
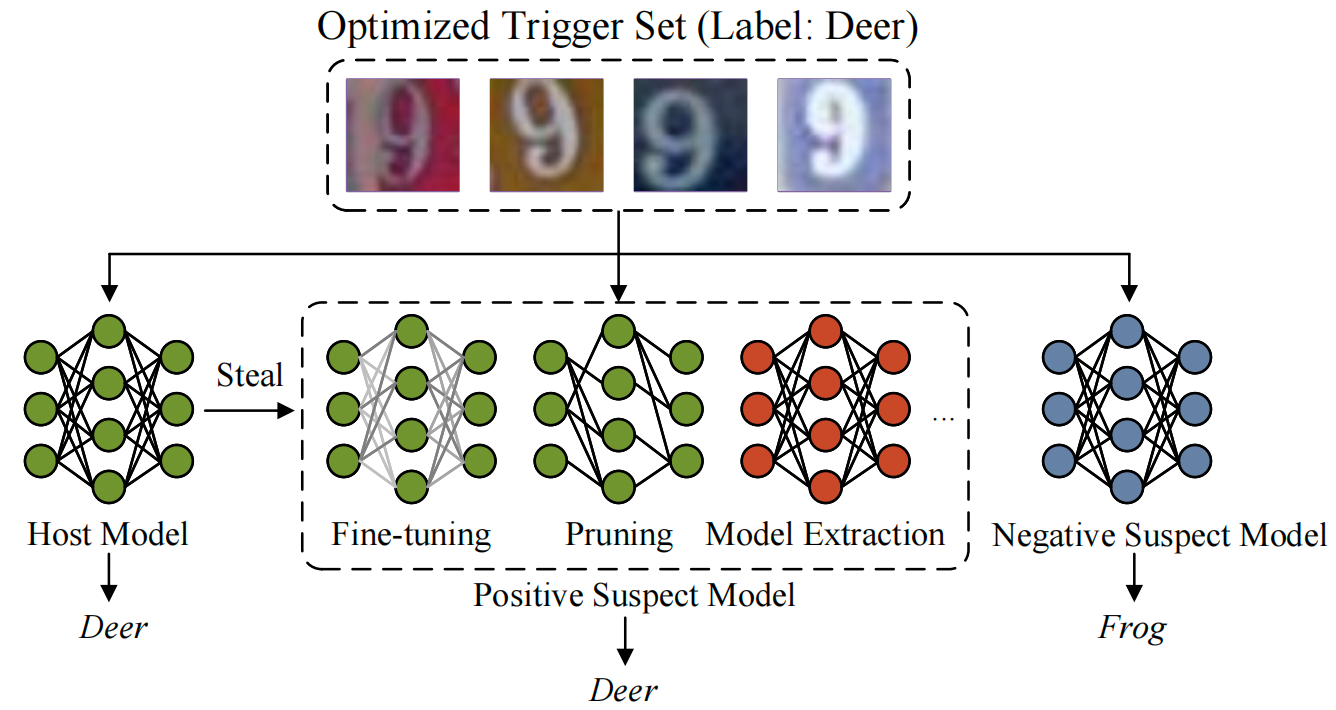
- Deep Neural Network Watermarking against Model Extraction AttackMM '23: Proceedings of the 30th ACM International Conference on Multimedia, 2023.
- VCMaster: Generating Diverse and Fluent Live Video Comments Based on Multimodal ContextsMM '23: Proceedings of the 30th ACM International Conference on Multimedia, 2023.
- Federated Learning with Label-Masking DistillationMM '23: Proceedings of the 30th ACM International Conference on Multimedia, 2023.
- Watermarks for Generative Adversarial Network Based on Steganographic Invisible BackdoorIEEE International Conference on Multimedia and Expo (ICME), 2023
- 抑制图像非语义信息的通用后门防御策略中国图象图形学报, 录用
- Removing Watermarks for Image Processing Networks Via Referenced Subspace AttentionThe Computer Journal, 2022.
- Steganography of Steganographic NetworksThirty-Seventh AAAI Conference on Artificial Intelligence (AAAI-23), 2023
- Imperceptible Backdoor Attack: From Input Space to Feature Representationthe 31st International Joint Conference on Artificial Intelligence (IJCAI 22), pp. 1736-1742, July 23~July 29, Messe Wien, Vienna, Austria, 2022
- HF-Defend: Defending Against Adversarial Examples Based on HalftoningIEEE 24th International Workshop on Multimedia Signal Processing, September 26-28, 2022, Shanghai, China.
- Privacy-Preserving Student Learning with Differentially Private Data-Free DistillationIEEE 24th International Workshop on Multimedia Signal Processing, September 26-28, 2022, Shanghai, China.
- Robust Backdoor Injection with the Capability of Resisting Network TransferInformation Science, 612(2022): 594-611.
- Perceptual Hash of Neural NetworksSymmetry, accepted.
- Invertible Image Dataset ProtectionIEEE International Conference on Multimedia and Expo (ICME) 2022, Taipei, Taiwan, 18-22 July, 2022
- Unlabeled Backdoor Poisoning in Semi-Supervised LearningIEEE International Conference on Multimedia and Expo (ICME) 2022, Taipei, Taiwan, 18-22 July, 2022
- Encryption Resistant Deep Neural Network Watermarking2022 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP 2022), 22-27 May 2022, Singapore, accepted.
- Object-Oriented Backdoor Attack Against Image Captioning2022 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP 2022), 22-27 May 2022, Singapore, accepted.
- Stealthy Backdoor Attack with Adversarial Training2022 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP 2022), 22-27 May 2022, Singapore, accepted.
- Joint Learning for Addressee Selection and Response Generation in Multi-Party Conversation2022 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP 2022), 22-27 May 2022, Singapore, accepted.
- Deep Neural Network RetrievalMM '21: Proceedings of the 29th ACM International Conference on Multimedia, October 2021, pp 3455-3463
- Fragile Neural Network Watermarking with Trigger Image SetInternational Conference on Knowledge Science, Engineering and Management (KSEM 2021), Tokyo, Japan, 2021
- Undetectable Adversarial Examples based on Microscopical RegularizationIEEE International Conference on Multimedia and Expo (ICME) 2021, Shenzhen, China, 5-9 July 2021
- On Generating JPEG Adversarial ImagesIEEE International Conference on Multimedia and Expo (ICME) 2021, Shenzhen, China, 5-9 July 2021
- Reversible Privacy-Preserving RecognitionIEEE International Conference on Multimedia and Expo (ICME) 2021, Shenzhen, China, 5-9 July 2021
- Key based Artificial Fingerprint Generation for Privacy ProtectionIEEE Transactions on Dependable and Secure Computing, 2018, DOI: 10.1109/TDSC.2018.2812192
- Dynamic adjustment of hidden node parameters for extreme learning machineIEEE Transactions on Cybernetics, 45(2): 279-288,2015.
- Evolutionary selection extreme learning machine optimization for regressionSoft Computing, 16: 1485-1491, 2012.

 ACM MM
ACM MM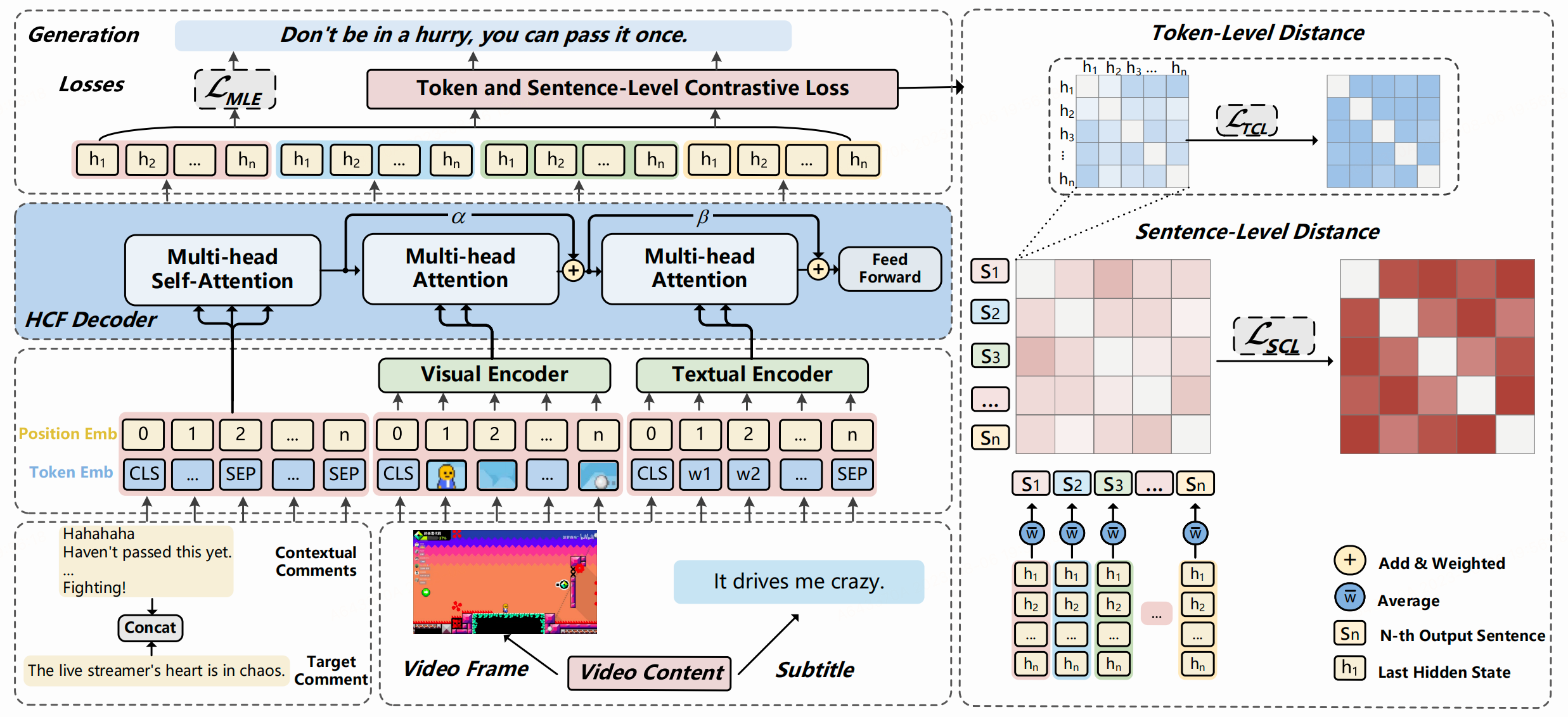 ACM MM
ACM MM