Information Hiding
The group mainly studies information hiding technology. We are particularly interested in 1) steganography for covert communication, including multimedia steganography, robust steganography and generative steganography, 2) digital and physical watermarking for copyright protection, including printing-resilient watermarking and deep-network-based watermarking schemes.
publication
- Securing Fixed Neural Network SteganographyMM '23: Proceedings of the 30th ACM International Conference on Multimedia, 2023.
- Cross-Modal Text Steganography Against Synonym Substitution-Based Text attackIEEE Signal Processing Letters, 2023
- Breaking Robust Data Hiding in Online Social NetworksIEEE Signal Processing Letters
- Image Sanitization in Online Social Networks: A General Framework for Breaking Robust Information HidingIEEE Transactions on Circuits and Systems for Video Technology
- STFF-SM: Steganalysis Model Based on Spatial and Temporal Feature Fusion for Speech StreamsIEEE Transactions on Audio, Speech and Language Processing
- Hiding Images in Deep Probabilistic ModelsThirty-Sixth Conference on Neural Information Processing Systems (NeurIPS), 2022
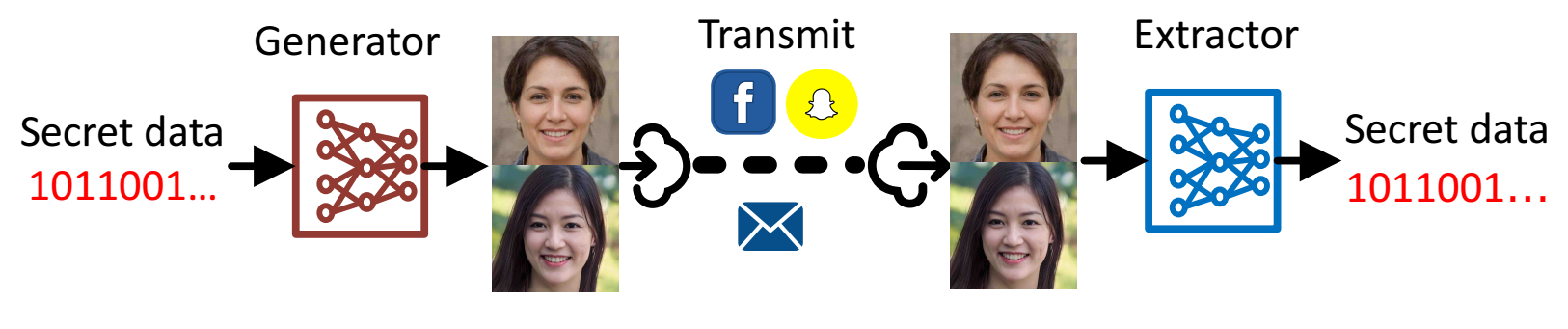
- Image Generation Network for Covert Transmission in Online Social NetworkMM '22: Proceedings of the 30th ACM International Conference on Multimedia, 2022
- Hiding Function with Neural NetworksIEEE 24th International Workshop on Multimedia Signal Processing
- Hiding Images into Images with Real-world RobustnessIEEE ICIP, 2022
- Generative Steganographic FlowIEEE International Conference on Multimedia and Expo (ICME), 2022, Taipei
- JPEG Steganography with Content Similarity EvaluationIEEE Transactions on Cybernetics, accepted.
- Image Steganalysis with Convolutional Vision Transformer2022 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), 2022
- Batch Steganography via Generative NetworkIEEE Transactions on Circuits and Systems for Video Technology
- Destroying Robust Steganography in Online Social NetworksInformation Sciences
- Diversity-based Cascade Filters for JPEG SteganalysisIEEE Transactions on Circuits and Systems for Video Technology
- How to Extract Image Features based on Co-occurrence Matrix Securely and Efficiently in Cloud ComputingIEEE Transactions on Cloud Computing
- Practical Cover Selection for SteganographyIEEE Signal Processing Letters, 27
- Steganography in Animated Emoji Using Self-ReferenceMultimedia Systems
- A New Steganography Method for Dynamic GIF Images Based on Palette SortWireless Communications and Mobile Computing, accepted.
- Defeating data hiding in social networks using generative adversarial networkEURASIP Journal on Image and Video Processing, 2020
- Adaptive Steganalysis Based on Statistical Model of Quantized DCT Coefficients for JPEG ImagesIEEE Transactions on Dependable and Secure Computing
- Steganography in Stylized ImagesJournal of Electronic Imaging
- Distortion Function for Emoji Image SteganographyComputers, Materials & Continua
- Steganography in Beautified ImagesMathematical Biosciences and Engineering
- On Improving Distortion Functions for JPEG SteganographyIEEE Access
- Distortion Function for Steganography in Texture Synthesized ImagesIn: Pan JS.
- Constructive Steganography Using Texture SynthesisIETE Technical Review
- Targeted Attack and Security Enhancement on Texture Synthesis Based SteganographyJournal of Visual Communication and Image Representation
- Multimedia Security: Novel Steganography and Privacy PreservingSecurity and Communication Networks, 2018
- Robust steganography using texture synthesisin: Proceeding of the Twelfth International Conference on Intelligent Information Hiding and Multimedia Signal Processing
- High-Capacity Framework for Reversible Data Hiding in Encrypted Image Using Pixel Prediction and Entropy EncodingIEEE Transactions on Circuits and Systems for Video Technology
- Optimized Lossless Data Hiding in JPEG Bitstream and Relay Transfer Based ExtensionIEEE Transactions on Circuits and Systems for Video Technology
- Reversible Data Hiding in Encrypted Images Using Adaptive Reversible Integer TransformationSignal Processing
- New framework of reversible data hiding in encrypted JPEG bitstreamsIEEE Transactions on Circuits and Systems for Video Technology
- A High Capacity Multi-Level Approach for Reversible Data Hiding in Encrypted ImagesIEEE Transactions on Circuits and Systems for Video Technology
- Reversible Contrast Mapping based Reversible Data Hiding in Encrypted ImagesIEEE International Workshop on Information Forensics and Security (WIFS), 2018, Hong Kong
- Reversible Data Hiding in Encrypted Images with Two-MSB PredictionIEEE International Workshop on Information Forensics and Security (WIFS 2018), Hong Kong
- Separable reversible data hiding in encrypted JPEG bitstreamsIEEE Transactions on Dependable and Secure Computing
- Lossless Data Hiding in JPEG Bitstream Using Alternative EmbeddingJournal of Visual Communication and Image Representation
- Reversible data hiding in encrypted image with distributed source encodingIEEE Transactions on Circuits and Systems for Video Technology
- Reversible data hiding in encrypted images based on progressive recoveryIEEE Signal Processing Letters
- Improved joint reversible data hiding in encrypted imagesJournal of Visual Communication and Image Representation
- Adaptive Reversible data hiding by extending the generalized integer transformationIEEE Signal Processing Letters
- Reversible visible watermark embedded in encrypted domainIEEE China Summit and International Conference on Signal and Information Processing, ChinaSIP 2015
- Reversible data hiding in encrypted JPEG bitstreamIEEE Transactions on Multimedia
- Efficient reversible data hiding in encrypted imagesJournal of Visual Communication and Image Representation
- Lossless data hiding in JPEG bitstreamJournal of Systems and Software
- Reversible watermarking via extreme learning machine predictionNeurocomputing
- JPEG Image Encryption with Adaptive DC Coefficient Prediction and RSPair PermutationIEEE Transactions on Multimedia, 2022

 ACM MM
ACM MM